An introduction to the UNIX tr utility
My Applied Cryptography and Computer Security class this semester has so far done a good job of introducing me to the (beautiful?) world of computer security and secure programming, which I do not think is something we generally learn in tandem with programming.
Part of our hands-on labs have involved completing a bunch of Capture The Flag challenges. I have learned a lot by attempting these CTF challenges on my own. The first in our series of CTFs required navigating a Linux server to find the flags. For me, this led to a deeper dive into different UNIX utilities and programs. One such utility was tr. I’ve come to appreciate how much one can learn about UNIX systems without having to google–just by reading the manual (man) pages. Thus, we will learn a bit about tr using only its man pages.
Background
We’re talking about security, so there are some things we need to understand. The most important in this case would be encryption. Encryption is a computer security technique used to secure files by transforming the file data into an unreadable format, such that this new format is unreadable until it has been returned to its original form (decryption).
Over the years, multiple methods/techniques of encryption (ciphers) have been developed. Of the ‘historical’ ciphers, perhaps the most popular has been the Caeser Cipher. It works by substituting each character of the plaintext (file to be encrypted) with another letter a fixed number of positions down the English alphabet. An implementation of the Caeser cipher is ROT13, a “simple letter substitution cipher that replaces a letter with the 13th letter after it in the alphabet.”
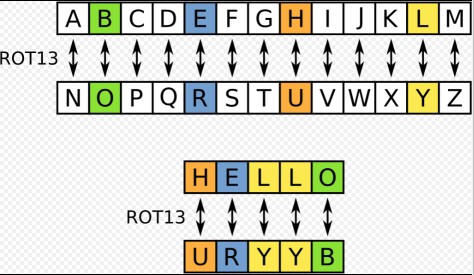
These types of ciphers that work using substitution are called substitution ciphers.
We’ll use ROT13 to illustrate the tr command.
The tr utility
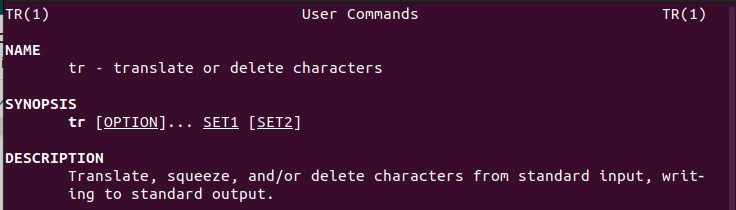
From the manual page above, we can see that tr is used to “translate, squeeze, and/or delete characters from standard input, writing to standard output.” This means that tr expects input from stdin and will display its output on stdout for whatever function it is used.
We also see that its usage includes a bunch of options and two sets. What does this mean, and what do the sets represent? Well, further down the man page we learn that “SETS are specified as strings of characters. Most represent themselves.”
From this description we can deduce that tr will take two sets of strings, one representing a sort of plaintext, and the other the corresponding key. It’s a way to tell the utility how to process whatever string you pass in from the standard input.
We will illustrate a practical usage using a plaintext and key from the ROT13 wiki linked above.
On running the tr utility with two string sets, the cursor begins to blink, indicating that it is waiting for output. When we enter a text into the standard input and hit the ‘Enter’ key, the text we entered is translated into another text based on the sets of strings we entered with the tr command.
An alternative way to pass input to the tr command is to ‘pipe’ output from another program, such as cat into it. Example:
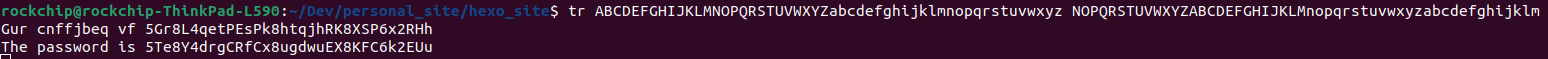
1 | cat data.txt | tr ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz NOPQRSTUVWXYZABCDEFGHIJKLMnopqrstuvwxyzabcdefghijklm |
Assuming that data.txt contained the text “Gur cnffjbeq vf 5Gr8L4qetPEsPk8htqjhRK8XSP6x2RHh”, the output of the command would still be “The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu”.
To end the program, use Ctrl + C or ⌘ + C on a Mac.
Some options that can be passed to the tr utility include:
-c, which would use the complement of SET1 for the translation,the
-toption which would truncate the length of SET1 to that of SET2 in the case that SET1 is longer. I think this truncation could be necessary due to the issue of repetition in the ciphertext that occurs when the plaintext is longer than the key. This repetition can be used to decipher the ciphertext.
Other options and their usage can be found in the manual page (man tr).
This has been a brief introduction to the tr UNIX utility. It’s a simple utility that is good playing around with simple cryptography. I hope you enjoyed the article. Comment any muddy points or other points of improvement, and I’ll be sure to clarify and update.
Cheers!